Lafayette CollegeTechnology Help
DUO Verified Push and Risk-Based Authentication
What is Risk-Based Authentication?
Authentication happens normally unless DUO determines an authentication attempt is unusual or higher risk through a combination of factors:
- User marked fraud: A user has indicated they weren’t responsible for a login by marking it as suspicious in the Duo Mobile app.
- Push harassment: A pattern of failed authentications is consistent with an adversary performing a targeted push harassment attack against a single user.
- Push spray: A pattern of failed authentications is consistent with an adversary performing a non-targeted push attack against multiple users.
- Unrealistic travel: A user attempts to authenticate from a new location that would be impossible to reach based on the past authentication time and location.
- Country code mismatch: The authentication device and access device appear to be in two different countries.
- Novel ASN: A user attempts to authenticate from an autonomous system number (ASN) not seen in the organization’s recent history of successful authentication.
If DUO detects a high-risk condition
The authentication will require a stronger second factor, typically a Verified Push, where you will need to enter the 6-digit number from the webpage into your DUO Mobile application.
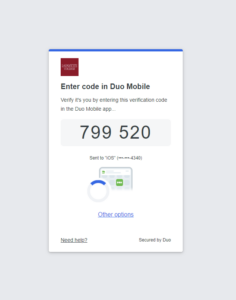
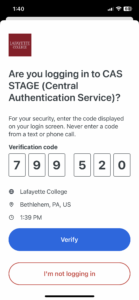
What if I don’t use the Duo application?
The following factors may be used during a high-risk authentication if the app is not available:
- Bypass codes – Bypass codes provided by the Help Desk
- Roaming and platform authenticators – WebAuthn FIDO2 security keys with biometric or PIN verification, and authenticators or biometric sensors built into the device like Touch ID or Windows Hello